SGX Hardware: A first look
by Jethro Beekman – Oct 8, 2015 – Updated: Dec 9, 2015. Filed under: English, Technology, Security, SGX.
Without much fanfare, Intel has released Software Guard Extensions (SGX) in Skylake. When I say “without much fanfare,” I mean practically only the following paragraph hidden on page 3 of a press fact sheet:
BETTER SECURITY. The Skylake architecture has been designed to enable better security, including Intel® Software Guard Extensions (Intel® SGX) that can provide an additional level of hardware-based protection by putting data into a secure container on the platform, and Intel® Memory Protection Extensions (Intel® MPX) that can help prevent buffer flow attacks. [What’s a buffer flow attack? Ed.] To be fully utilized, Intel SGX and Intel MPX require additional software capabilities, which will begin to be delivered by the ecosystem later this year.
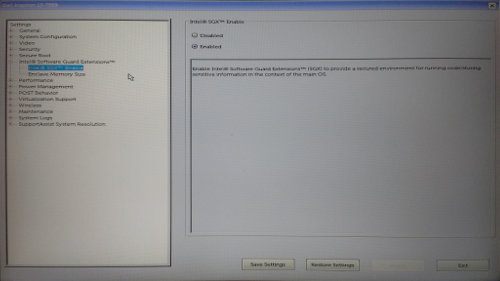
It has been extremely difficult to find actual hardware that supports SGX. BIOS support is required–the BIOS needs to set aside memory for the Enclave Page Cache (EPC)–but of course no vendor will mention anything about this on their website, nor will they (be able to) answer when you inquire regarding this specific issue.
To my delight, by using Google to search past week results for “intel sgx” for the last few months, I was finally able to find a driver download site that linked this Dell driver. According to Dell’s website, this driver is compatible with the following machine models:
- Inspiron 11 i3153
- Inspiron 11 i3158
- Inspiron 13 i7353
- Inspiron 13 i7359
- Inspiron 15 i7568
At first I couldn’t find these models mentioned anywhere, but a few days later the i7359 showed up at NewEgg and then at Frys. So, I drove to Sunnyvale (where Frys had the i7359-2435SLV in stock) and I can now confirm that SGX is real:
It’s interesting to note that SGX was disabled in the BIOS by default, so most consumers will not be able to benefit from this feature at all.
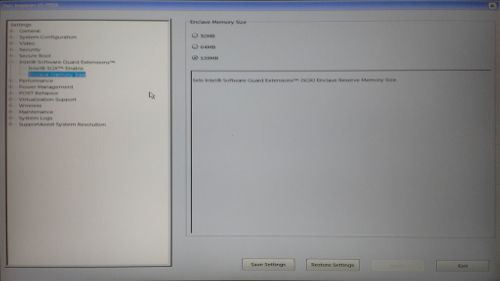
The maximum size of the EPC on this laptop is 128MB. This means that enclaves requiring more memory than that will need regular paging between the EPC and main memory. It’s not clear whether such a copy would require re-encryption of the page, the EPC itself is already encrypted so it might not be necessary.
The laptop comes with Windows 10 which runs excruciatingly slow–not surprising considering it only has 4GB of RAM. I installed Arch Linux on it because it’s one of the few distro’s that has an installer with a very recent kernel (4.2.2), required for such new hardware.
I collected some CPUID and MSR information to see what SGX features are supported:
CPUID
bit 2 (SGX) is set v 7h(0h) 00000000h 029c67afh 00000000h 00000000h Max. enclave size 2^31 bytes (32-bit mode) Max. enclave size 2^36 bytes (64-bit mode) | No extended SSA features supported | | SGX version 1 supported | |\/| v v vvvv 12h(0h) 00000001h 00000000h 00000000h 0000241fh all enclave attributes supported |\ all XSAVE bits supported vv vv 12h(1h) 00000036h 00000000h 0000001fh 00000000h EPC physical address 80200000h ////| |\\\\\\\ EPC size 93.5 MiB vvvvv vvvvvvvv vvvvv vvvvvvvv 12h(2h) 80200001h 00000000h 05d80001h 00000000hMSR
bit 18 (SGX_ENABLE) is set | bit 0 (LOCK) is set v v 3ah 00000000_00040005h (IA32_FEATURE_CONTROL)
I’m currently writing a simple Linux kernel driver to be able to actually use
SGX. I managed to generate a Page Fault using the ENCLS[EBLOCK] instruction,
so at least something seems to be working.
I really wish Intel would be more forthcoming with information about and developer support for SGX. The hardly-announced release and default-disabled BIOS setting don’t warrant much hope for the future of SGX.
In the mean time, I intend to write more blog posts in the near future as I try
to get SGX up and running. Here’s a cliff hanger for you: the Dell driver
package mentioned earlier contains a file aesm_service.exe that contains the
string “SGX EPID provisioning network failure.” I’ll try to tell you more about
it next time.
Update 2015-12-09: Please see my sgx-utils repository for any open-source SGX utilities, including a bare-bones development Linux driver.